- About us
- Knowledge
- Buddhism
- The Great Philosophers
- Indian Philosophy 1
- Indian Philosophy 2
- The Upanishads
- The Puranas
- Shaivism: A Brahmin-Hindu religion that worships Shiva as the supreme deity.
- Vishnu Puranua, Narayana Avatara or Dashavatara
- Ramayana: The Timeless Epic of Duty, Love, and Redemption
- Mahabharata
- The Bhagavadgita
- Jainism
- Greek & Roman Gods
- Ancient Angkor
- Burma and Mon Kingdom
- Dvaravati, Si Thep, Lavo, Supanburi, U-Thong, Phimai, Sema
- Sukhothai Kingdom
- Kingdom of Ayudhya
- Landmarks, Temples in and out of Ayudhya Island
- Places of interest in South East Asia & India Sub continent
- Lan Na Kingdom
- Lan Xang Kingdom
- Champa Kingdom
- Good Articles and Books
- Tribes and Ethnicities in Southeast Asia
- Important inscriptions in Southeast Asia
- Biography & Family Tree - Start from King Dhonburi the Great & The Five brave Soldiers
- The 44 Dynasties that ruled in Thailand Territorial Present
- Kamphoch Art Prasart in Thailand
- Somdej Than Buddhadas Indrabanyo's works
- Life is beautiful (Apirak's Version)
- Administration & Management
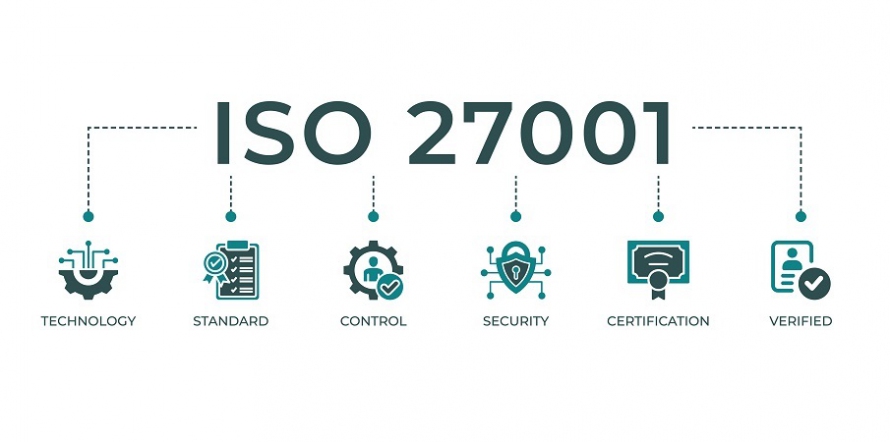
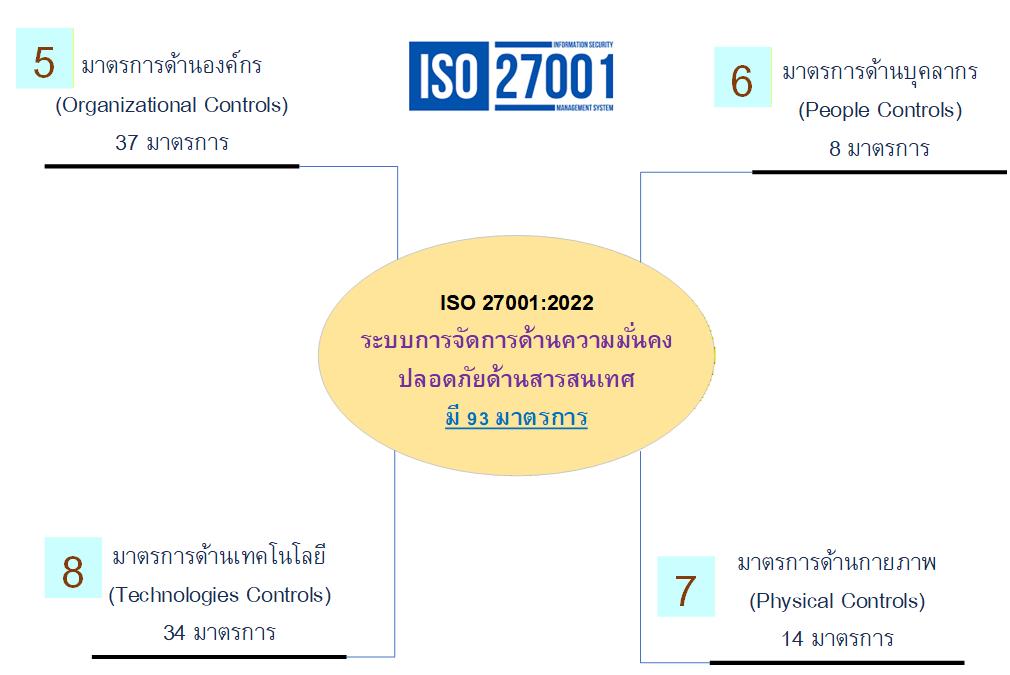
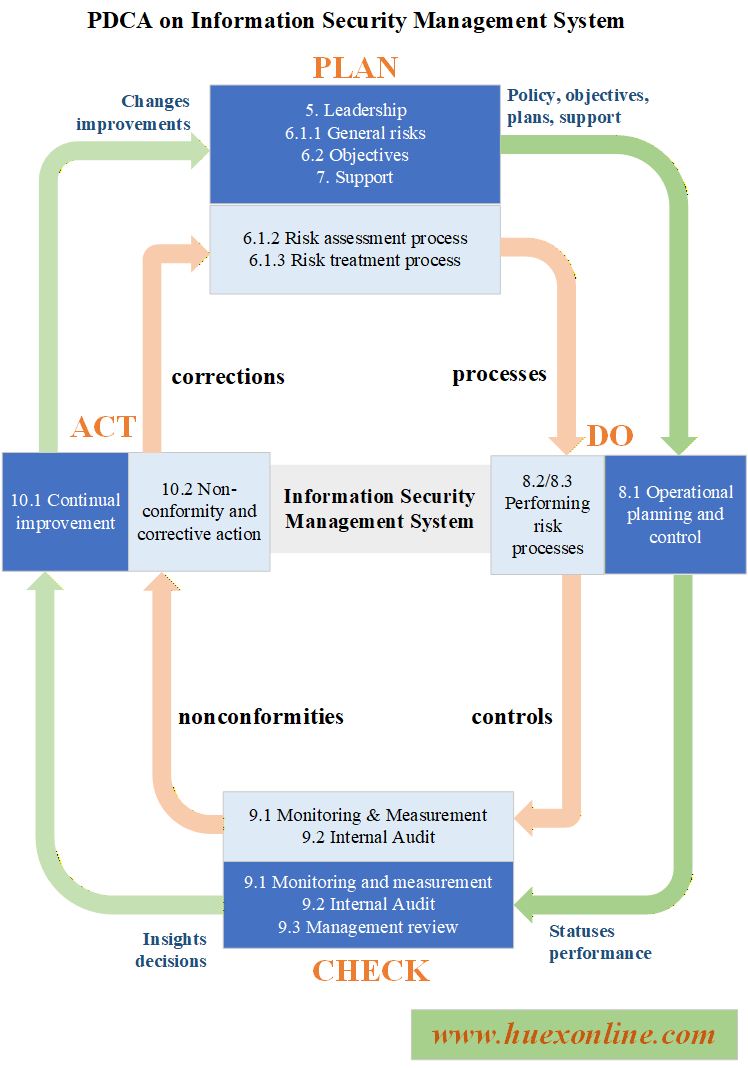
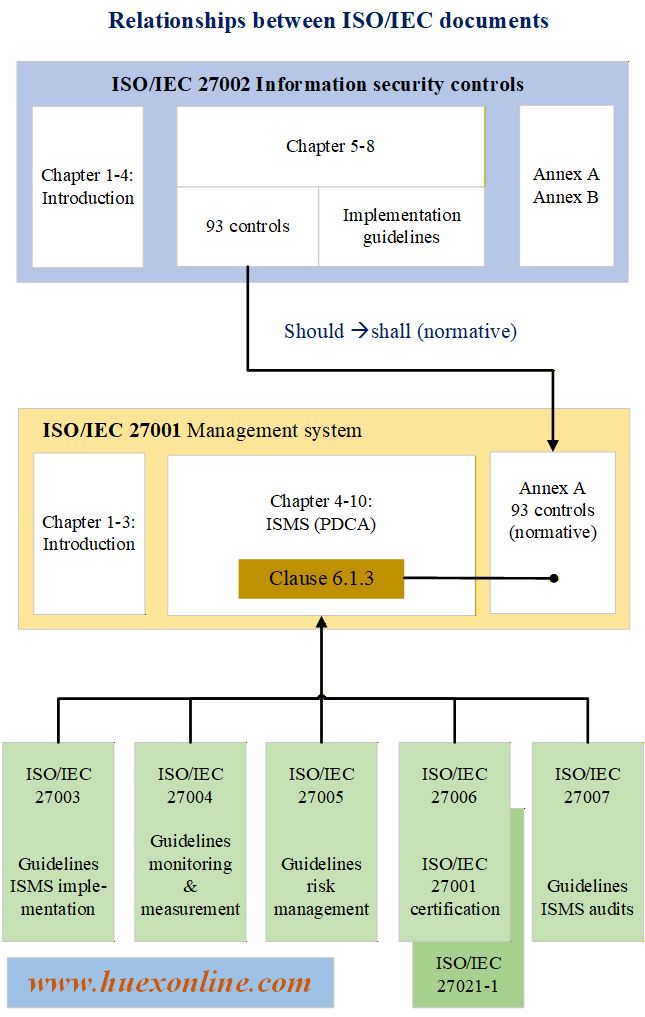
- Accounting & Finance, Auditing & Internal Control
- Biography
- Bank to The Poors
- Crazy the little things called vintage bicycles.
- The collected good things I
- Travel and Leisure by Apirak So Cools
- The smart girl meets the veteran uncle
- Download
- FAQS
- Contact us
MENU